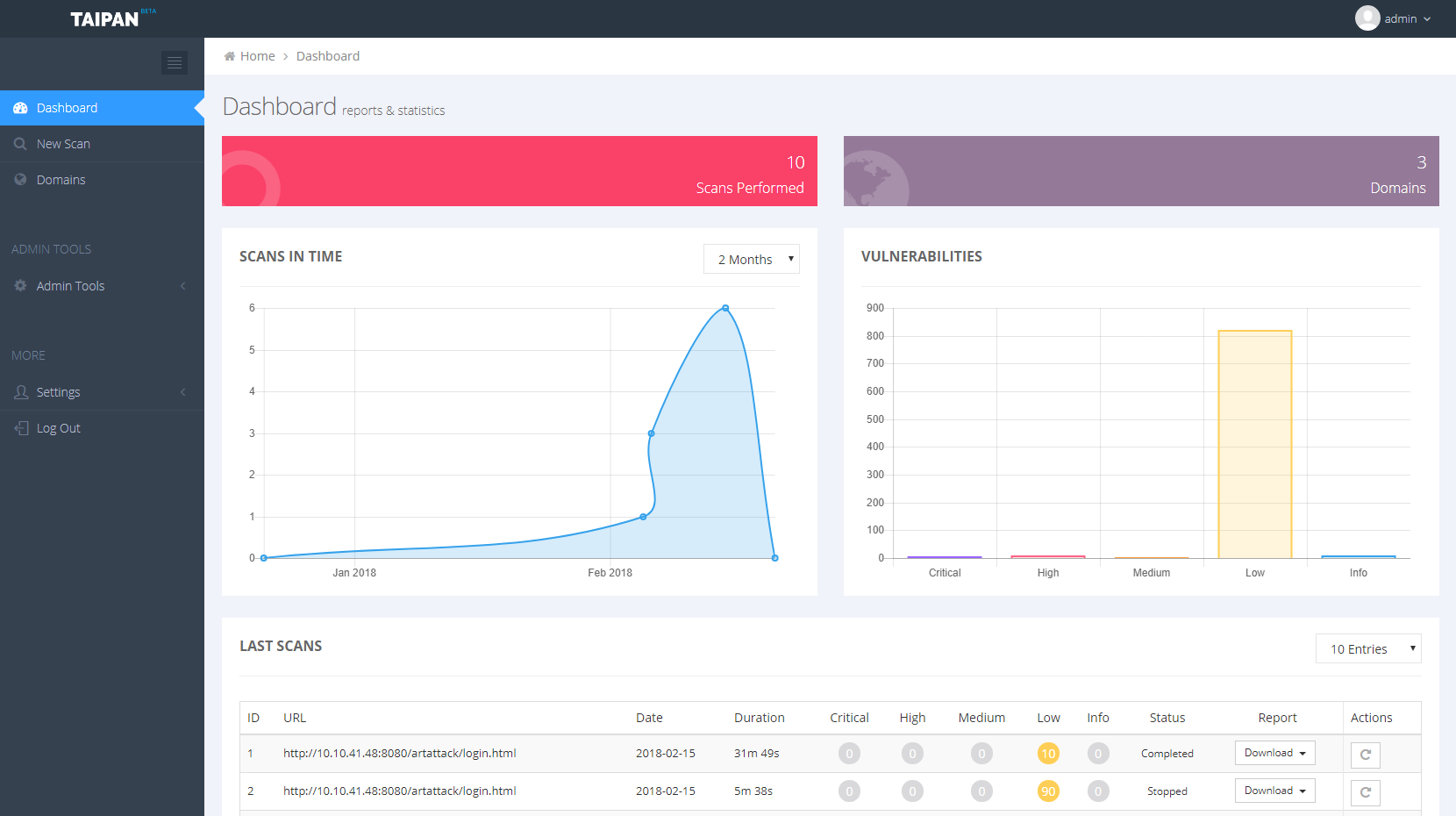
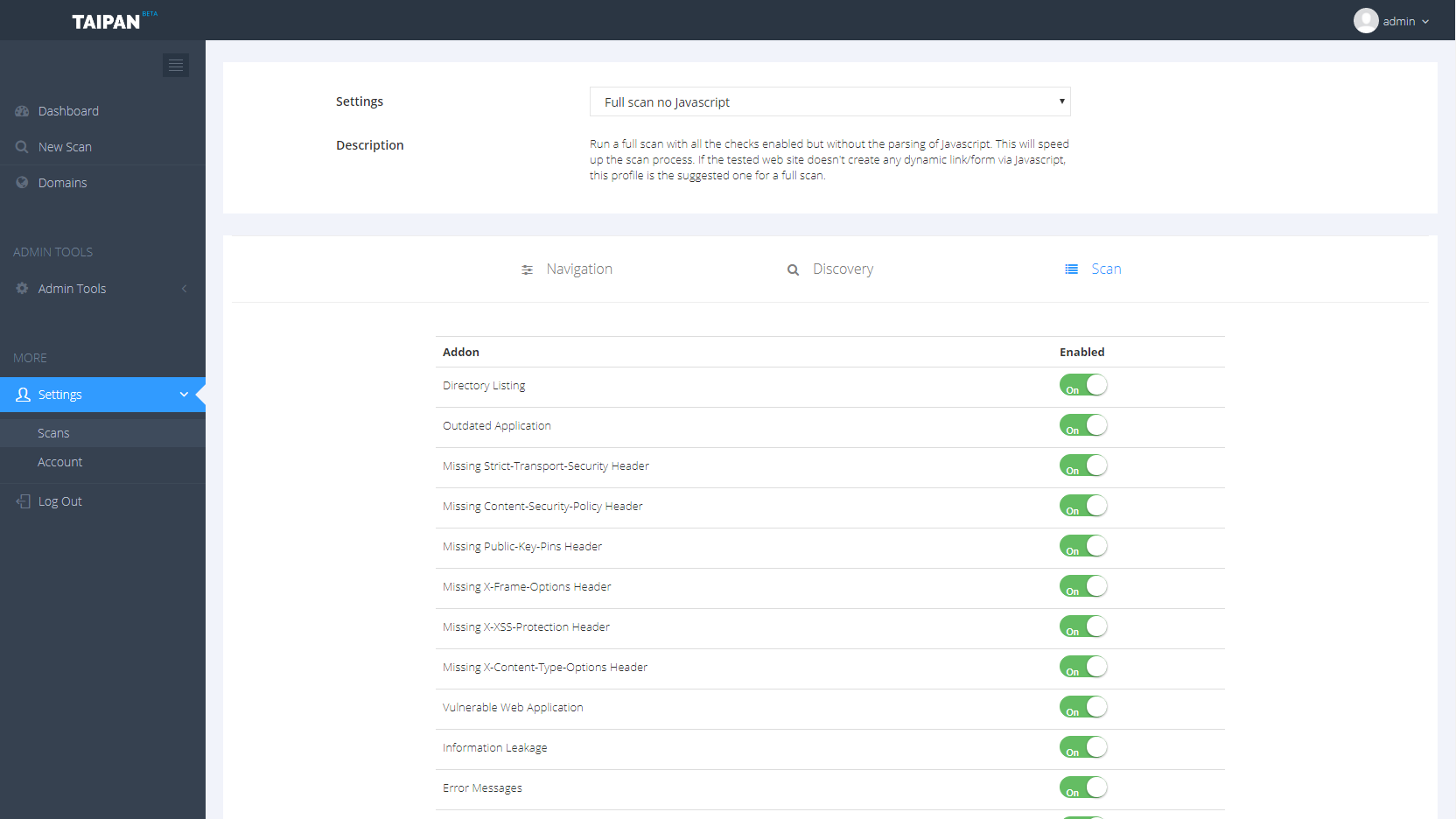
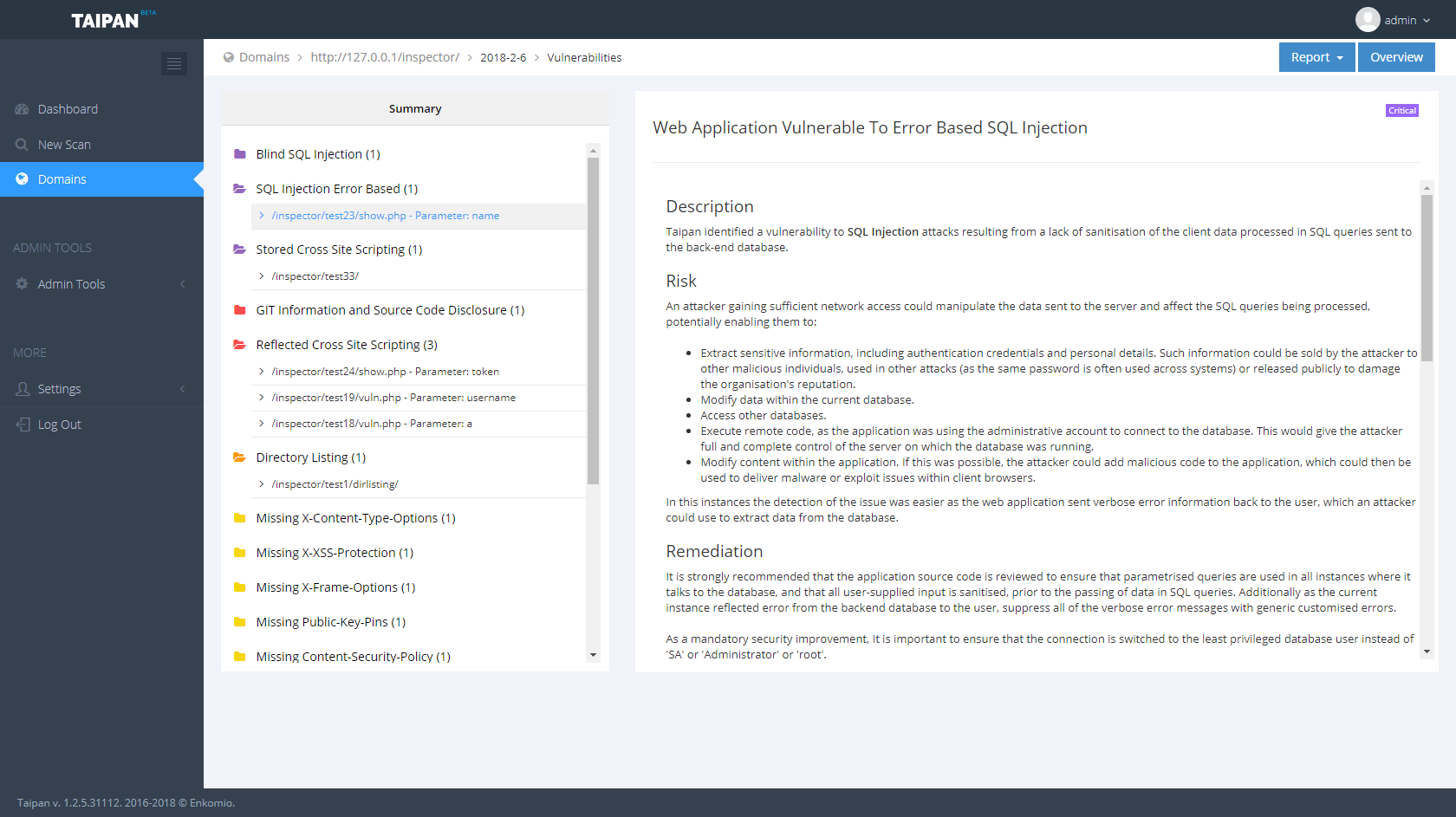
Taipan is an automated web application scanner which allows identifying web vulnerabilities in an automatic fashion. This project is the core engine of a broader project which includes other components, like a web dashboard where you can manage your scan or download a PDF report and a scanner agent to run on the specific host. Below are some screenshots of the Taipandashboard:
Changelog v2.4
- Generation of HTML report (Consultant edition)
- Improved Web Form Bruteforce AddOn (Consultant edition)
- Generation of a cleaner JSON report (Consultant edition)
- Improved hidden resource discovery component (avoided some false positives)
- Check for updates
- Minor bug fixing
Using Taipan
Taipan can run on both Windows (natively) and Linux (with mono). To run it in Linux you have to install mono in version >= 4.8.0. You can track the implementation of the new features in the related Kanban board.Scan Profile
Taipan allows scanning the given website by specifying a different kind of profiles. Each profile enables or disables a specific scan feature, to show all the available profile just run Taipan with the –show-profiles option.Scan/Stop/Pause a scan
During a scan, you can interact with it by set the scan in Pause or Stop it if necessary. In order to do so you have to press:- P: pause the scan
- S: stop the scan
- R: resume a paused scan
Launch a scan
To launch a new scan you have to provide the url and the profile which must be used. It is not necessary to specify the full profile name, a prefix is enough. Below an example of execution:
Taipan Components
Taipan is composed of four main components:- Web Application fingerprinter: it inspects the given application in order to identify if it is a COTS application. If so, it extracts the identified version.
- Hidden Resource Discovery: this component scans the application in order to identify resources that are not directly navigable or that shouldn’t be accessed, like secret pages or test pages.
- Crawler: This component navigates the website in order to provide to the other components a list of pages to analyze. It allows mutating the request in order to find not so common paths.
- Vulnerability Scanner: this component probes the web application and tries to identify possible vulnerabilities. It is composed of various AddOn in order to easily expand its Knowledge Base.